What is bitcoin? Is it the same as blockchain?
The quick answer is that bitcoin is not the same as blockchain.
What is bitcoin? Is it the same as blockchain?
The quick answer is that bitcoin is not the same as blockchain.
The Americans with Disabilities Act (ADA) is a civil rights law that prohibits discrimination against individuals with disabilities in all areas of public life, including jobs, schools, transportation, and all other places that are open to the general public.[1] When it comes to employment, the ADA provides that employers covered by the statute may not discriminate against “qualified individuals” with a disability with respect to employment matters.[2] The ADA defines such individuals as applicants or employees who, with or without reasonable accommodation, can perform the essential functions of the job.[3] Thus, the most contested issue becomes the question of whether or not the employee has a disability, as that term is defined by the Act.
One type of claimed disability that is increasingly the subject of litigation is obesity. Although courts initially were reluctant to recognize obesity as a qualifying disability for purposes of the ADA protections, courts are increasingly willing to consider obesity as a disability giving plaintiffs status to raise ADA claims.
Employers who collect fingerprints, face scans, or other biometric information such as retina or iris scans from employees or customers would be well-advised to ask permission and explain their purpose for collecting this data. If they don’t, they could be legally liable.
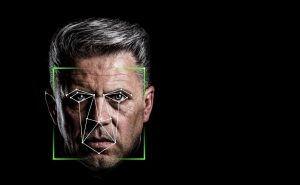 That’s in the wake of a relatively liberal interpretation of the Illinois Biometric Information Privacy Act (BIPA), which regulates the handling of biometric data, from the Illinois Supreme Court. The result of the ruling is that state-level lawsuits have greater latitude than those filed in federal court—but even suits dismissed at the federal level can sometimes be refiled in state court. The law remains in flux when it comes to what, exactly, constitutes biometric data. Photographs are not considered biometric identifiers, for example, but a software application that collects facial scans could be—and even federal courts have allowed for relatively broad interpretations on this front, mindful of the galloping pace of technological advances.
That’s in the wake of a relatively liberal interpretation of the Illinois Biometric Information Privacy Act (BIPA), which regulates the handling of biometric data, from the Illinois Supreme Court. The result of the ruling is that state-level lawsuits have greater latitude than those filed in federal court—but even suits dismissed at the federal level can sometimes be refiled in state court. The law remains in flux when it comes to what, exactly, constitutes biometric data. Photographs are not considered biometric identifiers, for example, but a software application that collects facial scans could be—and even federal courts have allowed for relatively broad interpretations on this front, mindful of the galloping pace of technological advances.
The Illinois Supreme Court in January defined an aggrieved person as anyone whose information is collected without their consent or knowledge, even if they were not harmed in the process, in the case Rosenbach v. Six Flags Entertainment Corp. (2019 IL 123186), issued on January 25 of this year and previously detailed on this blog. This means employers are liable for $1,000 in damages for each negligent violations and $5,000 for each intentional violations. For example, if an employer fingerprints employees each day as they check in and out of the office, and does not notify employees of the collection and storage of these fingerprints, the business could be fined $2,000 per day per employee. Perhaps not surprisingly, at least 90 class-action lawsuits alleging violations of BIPA have been filed since January in Illinois state courts.
Legal Marijuana Shouldn’t Mean Dazed and Confused Workers!
Starting on January 1 consumers will be able to buy marijuana for recreational use from licensed sellers. Pot users will no longer need to worry about fines or jail time – but employees will need to pay attention to their employers’ policies about drug screenings and the use of cannabis at work.
Employers should consider how they want to handle the legalization of cannabis in terms of workplace policies, written guidelines and staff training on the many issues that employers will be facing. Employers should take the time to review Section 10-50 of the “Illinois Cannabis Control Act” to see what protections they do and do not have. Among these are:
You might not realize it’s happening, and you definitely might not realize you have the right to object. But when you enter an airport in 2019, it’s possible that your airline—or the federal government—are scanning images of your face for their security-related purposes.

Say No to Airport Facial Recognition
This facial-recognition technology can be used during check-in, baggage drop, security and boarding. For the most part so far, it’s mostly only been deployed for international flights, to confirm passenger identity at the behest of Customs and Border Protection. But airlines and the Transportation Security Administration are considering doing so for domestic flights, as well.
Purchasing and flying a drone might seem like either a fun diversion or a new way of doing business. Professionals who do photography and videography, agriculture, weather forecasting, and increasingly construction are putting drones to commercial use, while they’re being piloted for package delivery through companies like Amazon and UPS.
Whatever use you have in mind for a drone, make sure you fully investigate federal, state and local laws on the subject, starting with those handed down a few years ago by the Federal Aviation Administration. For starters, drones being used for commercial purposes that weigh less than 55 pounds must have an Airworthiness Certificate, and the operator must have a Remote Pilot Airman Certificate.
Does your business have insurance to protect you against breaches of your cybersecurity? Turns out that’s not a simple “yes” or “no” question, and the answer changes constantly based on new cases being litigated and new types of breaches impacting companies.
Businesses need to take into account a wide range of factors in determining whether they have enough breadth and depth of insurance coverage to guard against any cyber liabilities. And it might be helpful to consult with an insurance broker who handles these types of policies.
First of all, you need to make sure you’re covered for your own damages resulting from such an incident. These can include the costs of forensic analysis to determine what happened, legal assistance, notification of individuals and regulators about a data breach, and any fines, penalties or other costs stemming from an enforcement action. Also, you need to be insured for any degree of business interruption.
Back in 2012, facing extreme reluctance from employers, the Equal Opportunity Employment Commission (“EEOC”) published guidance on whether and when to hire workers with criminal backgrounds who had done their time and were, hopefully, ready to be productive citizens and workers.
But employer reluctance to consider hiring ex-cons has waned in the past seven years as the economy has improved, the population has continued to age, and at least in Illinois, the population size has fallen due to people leaving for faster-growing states and fewer immigrants coming into the state. Meantime, more than 27,000 people got out of state prisons and more than 50,000 were released from Cook County Jail in 2018, and the National Employment Law Project estimates that 42 percent of Illinoisans have either criminal records or at least histories of arrest, which can include not only those found not guilty but those never formally charged in the first place.
It’s become somewhat easier for ex-cons (“the formerly incarcerated”) since the state legislature in 2014 prevented employers from asking on applications or early in the process about criminal history, making Illinois one of 23 states to take this step; private companies like Target had already done so. Then in 2016 the state changed licensing laws to make more than 100 occupations more accessible to those with criminal records, including areas like healthcare, accounting and real estate, while expanding the types of convictions that can be sealed—and therefore invisible.
 Americans talk about being “tethered” to their smartphones mostly from the standpoint of the time suck that’s involved and the tendency to miss what’s going on around us when we’re supposed to be working, spending time with family or friends, or (let’s hope not) driving down the highway. It’s hard to resist the offerings on your smartphone which now is millions times more powerful than NASA’s computers from the 1960’s.
Americans talk about being “tethered” to their smartphones mostly from the standpoint of the time suck that’s involved and the tendency to miss what’s going on around us when we’re supposed to be working, spending time with family or friends, or (let’s hope not) driving down the highway. It’s hard to resist the offerings on your smartphone which now is millions times more powerful than NASA’s computers from the 1960’s.
But one result of all that tethering – whether we’re texting, streaming music, getting directions from our GPS, or posting on social media – is that our smartphone is silently, relentlessly gathering all kinds of information about us. Your smartphone knows where you are, how you got there, with whom you’ve been communicating, and what you’ve been typing into your favorite search engine lately. It is this geolocation feature of smartphones that lets parents and spouses know the location of their family members, but it also provides a wealth of information to law enforcement personnel and those who understand how to retrieve this information. It has been quietly used by law enforcement agencies to obtain data about what smartphones have been active near crime scenes by issuing a subpoena to Google to recover the data. This was a feature story in the New York Times on April 13, 2019 which is part of an ongoing examination of the privacy issues associated with smartphones.
Although many people are vaguely uneasy about the variety and volume of information they cough up in their various apps, ultimately they are too tapped into the convenience and entertainment aspects to worry about controlling how much of their data is falling into the hands of marketers, retailers, the government and even foreign governments. Not to mention the brain cell and social skills deterioration that takes place.
Employers: Be cool with Pot Policies!
With Illinois adopting medical marijuana and looking to legalize recreational marijuana, lots of questions will be arise about what policies employers should adopt. Imagine workers passing a joint (or a bag of spiked gummy bears) around the water cooler or sharing a joint after work. Will employees be allowed to bring their baggie into work? And what about refusing to hire people who test positive for weed. These are murky waters we are wading into and it’s happening across the country. For now, it’s probably wisest for most Illinois employers to take the high road when it comes to disciplining or refusing hire those who smoke marijuana for medicinal purposes.
Illinois employers are allowed to implement a drug-free workplace policy that prohibits employees from possessing or using marijuana in the workplace and/or being impaired during working hours. And those provisions can apply even to those who hold medical marijuana cards under the Compassionate Use of Medical Cannabis Pilot Program Act, signed into law by former Governor Pat Quinn in 2013. However, only those employers that risk losing either a federal contract or federal funding for hiring those who use marijuana are permitted to discipline, or refuse to hire, a person who has a medical marijuana card or fails a pre-employment drug test because they use medical marijuana. The latter provision addresses the fact that marijuana stays in a person’s system up to a month after use.